
Finally getting it!

Finally getting it!
When resetting your Meijer password you get this on the form.
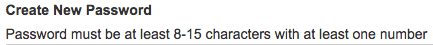
I assume they meant “between” instead of “at least” because those two words don’t make any sense with a range. After putting in my randomly generated password I got an error because I had used symbols that weren’t allowed, yet the instructions don’t say anything about symbols.
If you are developing a system and restricting password lengths to something so small with odd character restrictions, you’re doing it wrong. Allow 64 character passwords everywhere!
This week I came across a company domain I didn’t know we had.
It’s a very simple web service which allows you to store a secret, set an expiration, and then provides a URL so you can share it. When someone uses the special URL, if the expiration hasn’t passed they’ll be able see the secret.
Why would you need something like this? Maybe you want to share a password with someone. For security you shouldn’t send a password via email or text message, where it’s always visible in plain text. You can use something like this to send the URL and if you set it to expire after 1 viewing anyone else who finds the URL will not be able to view the secret.
This is what a 1 time view secret looks like when the URL is accessed…

If I try to reload the page…

Nifty, right?
We’ve had an internal Automattic tool called Once for years that does this same thing and I use it all the time when I need to send a password to a coworker. Give Quick Forget a try!
I have a simple local script, which logs into a remote server (my WordPress.com sandbox) via ssh to run a script there. After finishing, it runs another local command (unison) to pull down all of the files. The remote script is also very simple, calling svn update on several repos. If I ssh directly into the server and run the svn script, typing in passwords correctly shows up as a series of asterisks (****). Executing the same script remotely was showing the actual characters in my local terminal. Not ideal for security.
A Stack Overflow comment gave me what I needed. Wrap the ssh command with some stty commands.
stty_orig=`stty -g` stty -echo ssh USER@HOST './script.sh;' stty $stty_orig
This turns off the output of the password entry completely. I never type in the password since it’s a copy/paste from 1Password, so not having the asterisks is no big deal.
I’ve have several a lot of people post questions on other posts here at MDV asking how to unlock the iPod Screen Lock function if you forget the 4 digit combination/pass code, so I figured I would write up a short tutorial here to direct people to.
There are basically three ways to unlock the Screen Lock on your iPod:
Everything on your iPod will be erased.
This should not be a problem if you have all of your songs, videos, and other media stored in iTunes and you can synchronize once again after getting the iPod unlocked. Besides, if you don’t unlock your iPod it’s useless right? Learn how to Restore your iPod using the instructions from Apple’s site.
If your iPod is simply frozen, follow my instructions for an iPod Lockup Reset.
I had first ready about Hamachi a few months ago on Bryan’s site and finally got around to trying it out this weekend. It’s one slick piece of software. Much easier than setting up a VPN and all that junk.
With Hamachi you can organize two or more computers with an Internet connection into their own virtual network for direct secure communication.
Hamachi is fast, secure and simple. It is also free.
Think – LAN over the Internet.
Think – Zero-configuration VPN.
Think – Secure peer-to-peer.
Access computers remotely. Use Windows File Sharing. Play LAN games. Run private Web or FTP servers. Communicate directly. Stay connected.